Companies Should Implement ROI-Driven Cybersecurity Budgets, Expert Says
ompanies Should Implement ROI-Driven Cybersecurity Budgets, Expert Says
Discover the new models used to assign security budgets that succeed where traditional and outdated processes fail.
We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. This may influence how and where their products appear on our site, but vendors cannot pay to influence the content of our reviews. For more info, visit our Terms of Use page.
Image: Dzmitry/Adobe Stock
Cybersecurity budgets are up after enduring budget cuts and economic uncertainties, Forrester’s recent report reveals. Still, companies are struggling to combat cybersecurity threats and keep their companies safe.
Scale’s Cybersecurity Perspectives 2023 report reveals that most businesses (71%) are experiencing three or more security incidents, a 51% increase compared to 2022. Security teams struggle with talent gaps, are overwhelmed by alerts, and can’t find the right tools, despite security budgets increasing by 20% on average in large enterprises and 5% in mid-sized enterprises.
The problem seems to be insufficient funding, but for Ira Winkler, chief information security officer at CYE Security, it boils down to how cybersecurity budgets are determined and assigned. CYE is a SaaS platform and offers expert consulting for security leaders to maximize cybersecurity strategies and investments.
On July 20, I attended the Northeast Virtual Cybersecurity Summit to gain insights into new methods that can be used to successfully change the way cybersecurity budgets are allocated.
Jump to:
- Shifting outdated mindsets to business-driven models
- Getting buy-in from executives and boards
- ROI-driven cybersecurity budgets
- Final thoughts: Setting priorities
Shifting outdated mindsets to business-driven models
At the summit, Winkler explained that the cybersecurity industry has shifted from protecting software and hardware under an information resources management approach to protecting the information that moves through systems with the emergence of chief information security officers. However, companies still allocate cybersecurity budgets with an outdated mindset.
Cybersecurity economics, cybersecurity valuations and risk-approach models are emerging fields that can quantify risks, countermeasures and return on investment to maximize system security and minimize losses. However, they are poorly understood and not applied.
- Cybersecurity economics is the study of the economic costs and benefits of cybersecurity. It aims to understand how organizations can make optimal investment decisions in cybersecurity given the risks they face.
- Cybersecurity valuations are the methods used to estimate the value of cybersecurity assets, which might include data, systems and networks.
- Risk-approach models are used to evaluate a threat’s risks and their consequences. Different factors are considered in risk modeling, including the likelihood of a cyberattack, the potential impact of a cyberattack and the cost of mitigating the risks.
“What does a ransomware incident cost?” Winkler asked attendees. “Most people don’t really know. And more importantly, in cybersecurity, we don’t know how much a non-incident costs us. We don’t track how well we stop things at all, for the most part. And that’s a fundamental lack of business discipline and business thought processes.”
Must-read security coverage
- 8 Best Penetration Testing Tools and Software for 2023
- 6 Best Cybersecurity Certifications of 2023
- How Generative AI is a Game Changer for Cloud Security
- New Malware Targets 97 Browser Variants, 76 Crypto Wallets & 19 Password Managers
Winkler explained that this lack of a business approach is unique to cybersecurity departments. Other areas, such as finance and accounting, supply chains and operations and manufacturing, do not allocate budgets arbitrarily. For example, modern factories usually have a full understanding of what a specific downtime costs and what the value is when the factory is up and running.
In a data-driven era, cybersecurity teams must have insight into outages, incidents and any other factor that affects performance and the company’s bottom line. With this information, executives can make data-driven decisions on budgets based on economic impact, risks and losses versus ROI and gains.
Getting buy-in from executives and boards
It’s no secret that one of the biggest challenges CISOs and other security leaders face is getting buy-in from boards and executives. Additionally, security teams face increased pressure from boards as their roles and responsibilities expand.
In the latest ClubCISO Report 2023, 62% of CISOs surveyed listed leadership endorsement as the most critical factor in fostering a better security culture. Despite increased alignment between security teams, executives and boards, 20% of those surveyed still say that the lack of buy-in and support impacts their companies’ security.
“Unfortunately, in cybersecurity, we have people who don’t know how to discuss budgets with management,” Winkler said.
According to Winkler, as long as security leaders do not take more scientific and business approaches to budgeting, they will always receive random allocations and get unwanted results. When pitching executives for buy-in, security leaders must be well informed on acceptable risk levels, how effective their countermeasures are and what the top vulnerabilities cost them.
Winkler said that only budgets that minimize risks and potential losses should be presented to management. When a board or an executive suggests cutting a budget, the security team must know how much that cut will cost the company. This method presents better information to executives, allowing them to make better decisions, and helps get buy-in. It also relieves security leaders of responsibilities as they inform company management about the risks before they happen.
“Knowing how to present cybersecurity programs in business terms is the most effective way to get the budget you need,” Winkler told the audience of security experts.
Privacy breaches; compliance issues; U.S., EU and international laws; insurance costs; fines; and outages driven by natural disasters should also be incorporated into security programs, according to Winkler.
ROI-driven cybersecurity budgets
Cyber-risk quantification is not a new concept, but risk-approach models are still in their infancy. While organizations like Gartner report on its increased adoption and top vendors like Bitsight, SecurityScorecard, Corax, UpGuard and Squalify offer it, implementing it all can be overwhelming.
Winkler assured that risk-approach models should not be overcomplicated. “This is the only diagram I have in my company,” Winkler said (Figure A).
Figure A
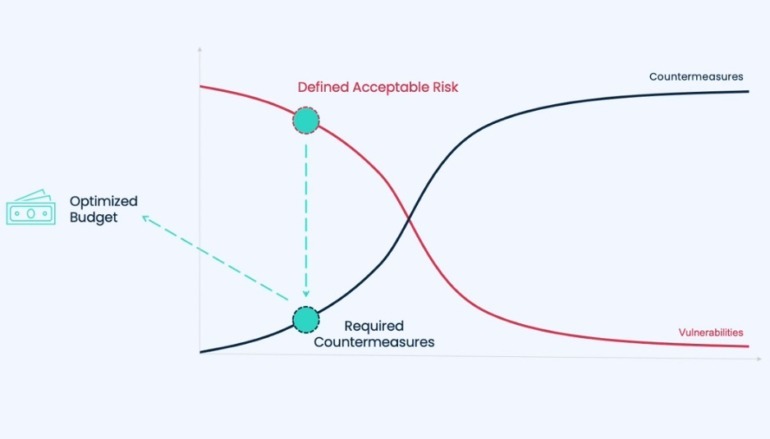 Ira Winkler’s risk-approach cybersecurity model. Image: Ira Winkler’s presentation at the Northeast Virtual Security Summit.
Ira Winkler’s risk-approach cybersecurity model. Image: Ira Winkler’s presentation at the Northeast Virtual Security Summit.
The red line in the graph represents a company’s vulnerabilities, and everything under the red line represents potential losses. When a company starts risk-modeling without countermeasures, vulnerabilities and potential losses are at their maximum; as countermeasures are implemented and increased, potential losses begin to go down. However, Winkler explained that there is a catch.
When managing risks, most people think a company should add as many countermeasures as possible to reach a minimum value of vulnerabilities and reduce potential losses to zero. However, that is not the case because the cost of implementing the required countermeasures to bring vulnerabilities to a minimum is usually exponentially higher than the cost of vulnerabilities.
A company does not want to see the cost of its countermeasures higher than the cost of its losses and also not equal to them. Achieving the right balance can be challenging.
“What you want to do is figure out what I call the risk optimization point,” Winkler explained. “And that’s where essentially you figure out the potential loss you’re willing to accept and then what countermeasures are theoretically going to get you there.” The concept is much like long-term investments.
The challenge for security teams and executives alike is to accept that no matter what they do, they will always face potential losses and risks. Additionally, a company-wide culture that has been assigning cybersecurity budgets for decades by simply adding a 5% to 20% increase to the budget of the previous year must be changed.
Allocating “an arbitrary budget gives you arbitrary results,” Winkler said. He urged security experts at the event to map threat sources, assets, vulnerabilities and potential losses to understand their exposure. The cybersecurity expert also presented a risk equation to explain how companies can quantify factors, highlighting the disruptive power of AI and machine learning to drive these mathematical calculations (Figure B).
Figure B
 Ira Winkler’s risk equation. Image: Ira Winkler’s presentation at the Northeast Virtual Security Summit.
Ira Winkler’s risk equation. Image: Ira Winkler’s presentation at the Northeast Virtual Security Summit.
Final thoughts: Setting priorities
Setting priorities and implementing the highest value of countermeasures that generate the highest ROI while analyzing the cost and probability of vulnerabilities may seem like a rigged game of numbers where incidents and losses are bound to happen. However, accepting minimum losses and incidents far outweighs other alternatives.
Traditional methods used to allocate cybersecurity budgets have become outdated, and the consequences associated with these types of approaches are well documented in threat reports that show the yearly rising costs of threats.
More funding and more tools do not necessarily translate into more security. Security resources must be properly allocated, and the costs of each countermeasure solution must be balanced against the cost of attacks.
While other factors need to be considered, such as companies’ ethical responsibilities to protect each customer, partner and system, a data-driven business approach to cybersecurity budgets can undoubtedly change the cybersecurity industry.
Subscribe to the Cybersecurity Insider Newsletter
Strengthen your organization’s IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices.
Delivered Tuesdays and Thursdays
Published: August 3, 2023, 1:56 PM EDT Modified: August 3, 2023, 1:56 PM EDT See more Security
Also See
- Survey: Cybersecurity budgets aren’t matching cybersecurity challenges (TechRepublic)
- HackerOne: How the economy is impacting cybersecurity teams (TechRepublic)
- Year-round IT budget template (TechRepublic Premium)
- Cybersecurity: More must-read coverage (TechRepublic on Flipboard)














