AMD’s Inception Fix Causes Up to 54% Performance Drop
A week ago, news about AMD’s Inception vulnerability broke, and the first deep dive into the performance impact of mitigations has been published. Linux-centric Phoronix has just uploaded eight pages of test results. Using an AMD Epyc 7763 (Zen 3) based system, running Linux (of course), the site tested a plethora of apps and tabulated before and after-patching results. Depending on workload, you might not see much difference — however, some tasks were up to 54% slower on a patched system.
|
Test process |
No patch result |
Worst patch performance |
|---|---|---|
| MariaDB 4096 (queries/s) |
590 |
274 (-54%) |
|
DaCapo (time, ms) |
3993 |
5305 (+33%) |
|
Linux Compilation defconfig (time, s) |
31.19 |
40.09 (+29%) |
|
Gimp rotate (time, s) |
9.444 |
12.096 (+28%) |
|
OpenRadioss (time, s) |
77.48 |
99.04 (+27%) |
|
Apache Spark (time, s) |
4.91 |
5.74 (+17%) |
|
7zip (MIPS) |
384374 |
334812 (-13%) |
|
Blender 3.6 (render, s) |
27.34 |
27.73 (+1.4%) |
|
Firefox Speedometer (runs / minute) |
347 |
343 (-1.2%) |
Data from Phoronix benchmarking
For the above table we looked at some of the worst results, as well as some of the test results from more-familiar apps like 7zip, Blender, and Firefox. Those three familiar apps don’t suffer too much from the AMD Inception mitigations. Of the three, compression app 7zip seems to be the most affected — but how long do you spend de-compressing files in an average day?
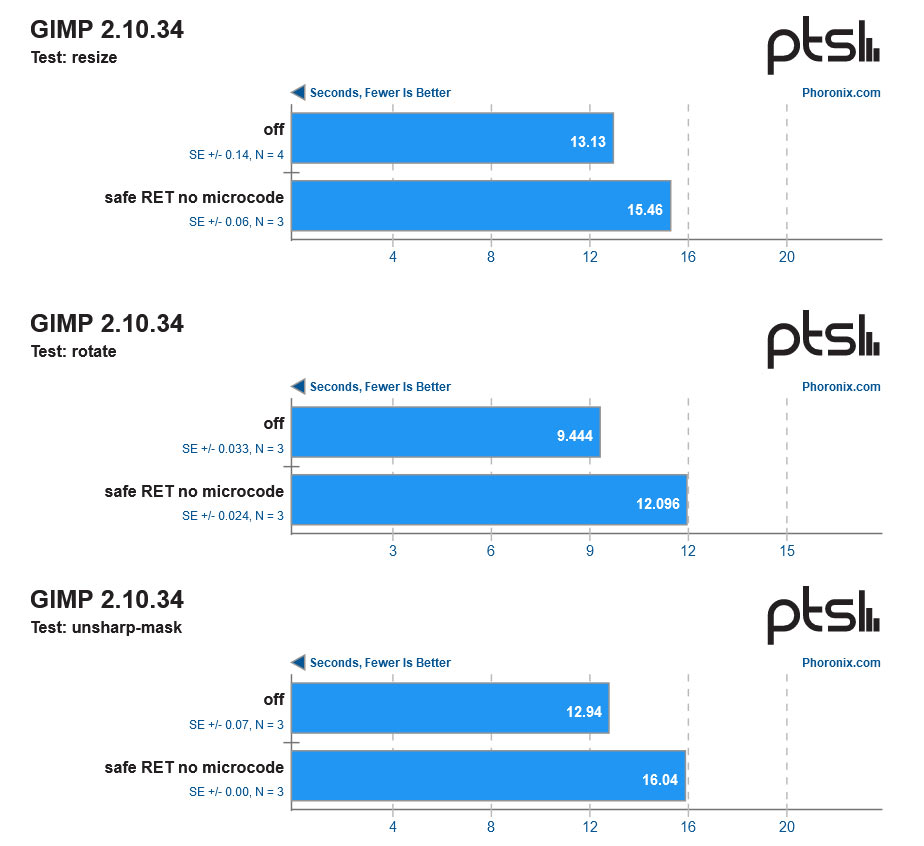
Much more serious performance consequences are observed in applications that work on databases, code compilation, engineering, and image processing. The worst result we saw, with MariaDB, shows database operations were severely impacted on a patched Epyc system.
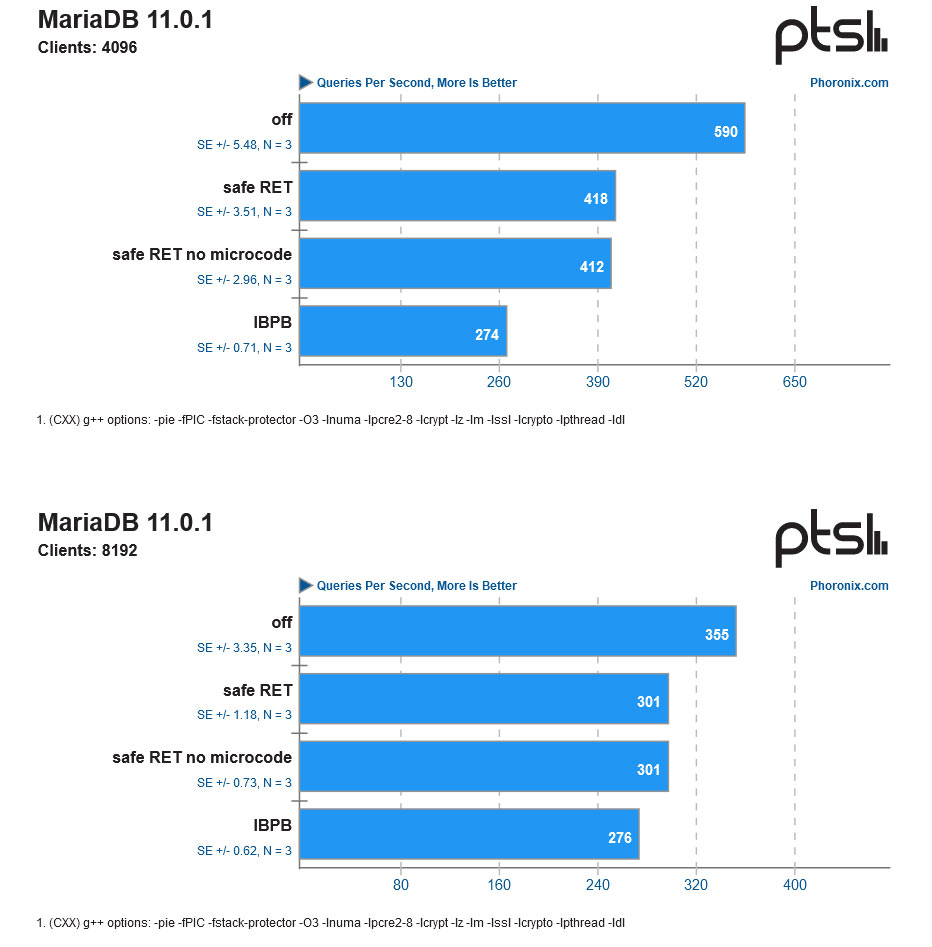
If you head over to Phoronix for a closer look at the data and a wider selection of results you will see that the results sometimes show more than just the AMD Inception mitigation being ‘off’ or ‘on’. There will be up to three levels of patching with different configurations — some with purely kernel-based mitigations, others with the newest microcode, and another with the most secure Indirect Branch Prediction Barrier (IBPB) mitigation. Please note that IBPB was frequently (but not always) shown to be the worst performer of all mitigations. The default AMD Linux mitigation is ‘safe RET mode’.














